Short Bytes: The researchers from Tel Aviv University and Technion have found a way to steal encryption keys from “safe” air-gapped machines. The attack was launched from another room and the target was completely offline. Known as side-channel attack, it doesn’t try to break the encryption by exploiting encryption algorithm weakness or brute force attack. Instead, researchers captured the electromagnetic waves emitted during the decryption process.

In recent times, hackers are aggressively targeting the air-gapped machines, which are considered super-secure. These systems are disconnected from the internet so that a hacker is unable to deploy any attack remotely via internet or any network.
Do you remember the researchers who used a homemade device “PITA” to steal keys and data from your PC? That device captured the stray radio waves emitted by your computer’s processor.
Going one step ahead, the same researchers from Tel Aviv University and Technion have showcased a way (PDF) to squeeze data from such “safe” air-gapped machines. Interestingly, the hacked computer was located in an adjacent room, across a wall.
This attack extracts the secret decryption keys within seconds from the target machine located in other room with the help of lab equipment (antenna, amplifiers, software-defined radio, and laptop) worth $3000. The experts claim that with more lab research, the equipment could be simplified.
The attack was completely non-intrusive and the targets were not touched. Known as side-channel attack, it doesn’t try to break the encryption by exploiting encryption algorithm weakness or brute force attack. Here, the method used to break the encryption was capturing the electromagnetic waves emitted during the decryption process.
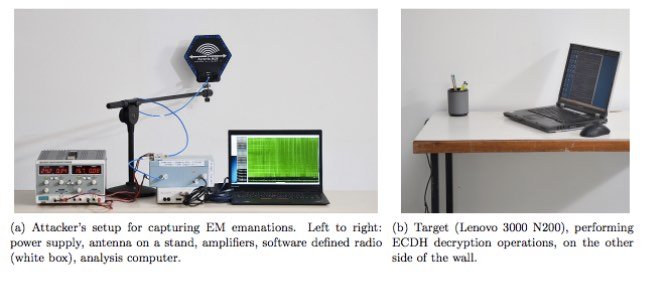
After obtaining the private key from a laptop running GnuPG, the researchers sent a specific encrypted message to the target. Now, the EM leakage of the target was measured repeatedly to reveal the key. The secret key was obtained after studying 66 decryption processes (each lasting 0.05 seconds) in 3.3 seconds.
At the moment, such ways to hack systems is very much limited to research. But, researchers feel that in not-so-distant future, hackers could use these techniques by making them more accessible and cheaper.
“Our work is most pertinent to systems that are carefully protected against software attacks, but—as we show—may be wide open to inexpensive physical attacks,” researchers said.